One of the major problems that I have had on my Windows PC is a lack of security beyond the operating system. Although we can set a strong password and use two‑factor authentication (2FA) to prevent unauthorized access to our PC, our hard disks or drives remain insecure. Someone can easily steal your laptop, boot it up with new OS and its back to business. Your hard disk can also be externally connected to any other computer, and your data will be easily accessible.
This problem has been bugging me a while especially with government agencies confiscating people devices on arrest. Not to imply that I have anything illegal to hide but it is important to ensure that all of our data remains safe especially in the modern digital age where data is everything. Here are some of the most effective ways to secure your hard disk.
Full-Disk Encryption
One of the most surreal ways of protecting your data is full-disk encryption, which ensures that all the data in your hard drive remains unintelligible without the correct key to decrypt it. This method is the most effective but make no mistake since it carries a higher risk and can lead to 100% data loss if your lose your key or recovery codes.
For windows OS, the best choice for encryption is BitLocker. According to Microsoft, BitLocker is a Windows security feature that provides encryption for entire volumes, addressing the threats of data theft or exposure from lost, stolen, or inappropriately decommissioned devices.
BitLocker provides maximum protection when used with a Trusted Platform Module (TPM), which is a common hardware component installed on Windows devices. The TPM works with BitLocker to ensure that a device hasn't been tampered with while the system is offline.
In addition to the TPM, BitLocker can lock the normal startup process until the user supplies a personal identification number (PIN) or inserts a removable device that contains a startup key. These security measures provide multifactor authentication and assurance that the device can't start or resume from hibernation until the correct PIN or startup key is presented.

BitLocker is therefore effective as it prevents users from booting the drive without entering the key or the PIN to unlock the drive. However, there is no known way for a user to access their data if they lose their BitLocker key or forget the PIN, which makes it important for users to make sure they back up their keys.
Another point to note is that BitLocker is also only available in Windows Pro and Enterprise editions. It also only works on Windows, which means you cannot use the drive in any other OS. An alternative solution is Veracraft, which is a free and open source disk encryption that works in all OS, including Linux and Mac.

For Mac Users, there is FileVault, a built-in encryption capability, to secure all data at rest. FileVault uses the AES-XTS data encryption algorithm to protect full volumes on internal and removable storage devices.
FileVault on a Mac with Apple silicon is implemented using Data Protection Class C with a volume key. On Mac computers with Apple silicon and Mac computers with the Apple T2 Security Chip, encrypted internal storage devices directly connected to the Secure Enclave leverage its hardware security capabilities as well as that of the AES engine. After a user turns on FileVault on a Mac, their credentials are required during the boot process.
File Protection
In some cases, files or folders need to be secured to ensure they are inaccessible, even when the encrypted drive has been unlocked. For example, if you leave your PC unlocked or someone in your family is using it, and you have some sensitive files that you need to keep hidden and secure, then you should consider using a password manager.
You might need to safeguard all of your most private and sensitive data in a way that most people would either be unable to access at all, or at least provide enough of a prolonged struggle that (again, most people) would simply be less likely to invest their time trying to gain access.
These files or folders can contain things not meant for family members or others to see. One potential solution to this is to store the information in an external hard drive that is encrypted using Veracrypt, or use Veracrypt to encrypt individual files and folders.
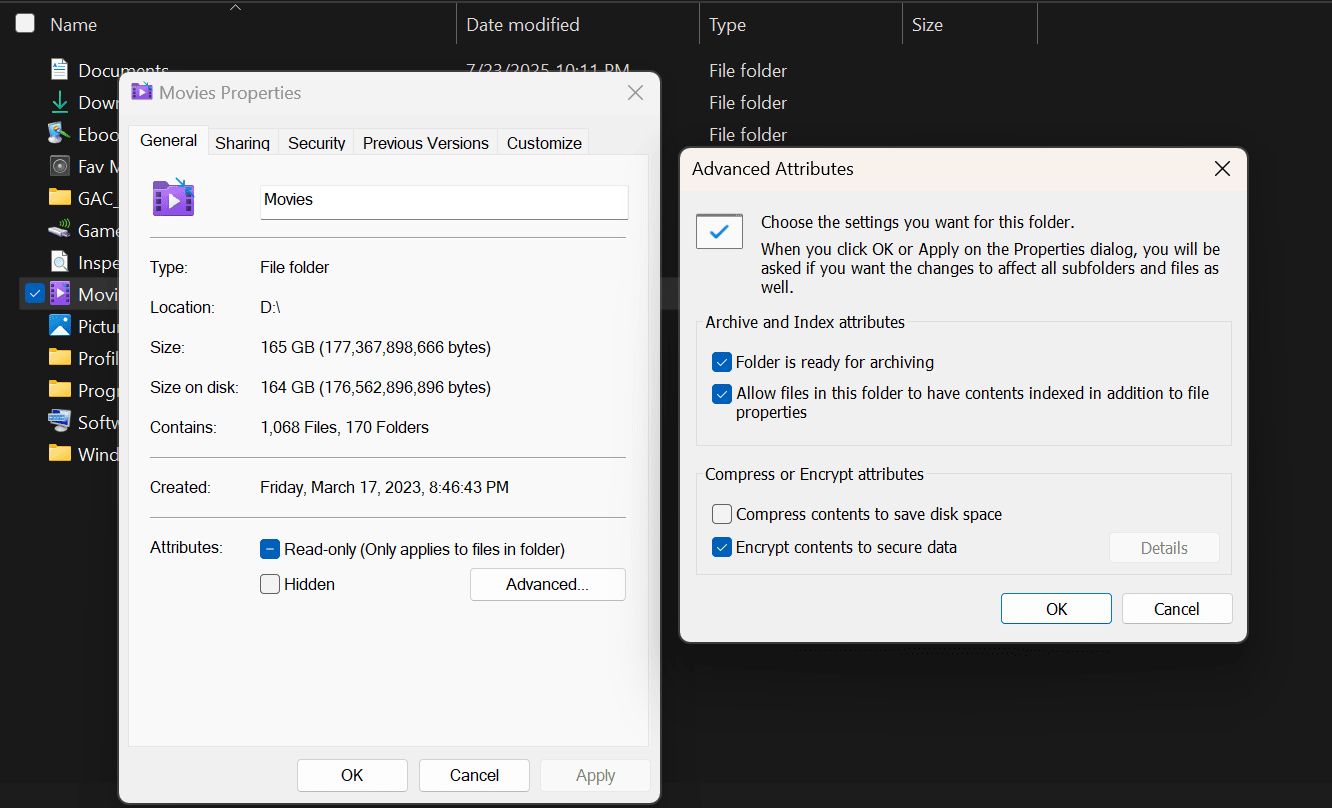
In Windows, you can right click on the folder or file, select properties > advanced > encrypt contents to secure data > apply. This will help encrypt the folder or file and prevent it from read/write access. Once the process is completed, a lock will be added to the folder, which means it is encrypted and “locked” from public access.
Password and Two Factor Authentication
Securing and encrypting your drive requires you to use a password and create a recovery key incase you forget this password. Veracraft recommends that you use a very unique and strong password with more than 20 letters to prevent data loss from brute force attacks. To ensure your data is safe, Enable two‑factor authentication (2FA) on systems or disk‑encryption solutions that support PIN + token or biometric + password for added protection.
You can also consider buying a YubiKey. A YubiKey is a small USB or NFC-based hardware device that provides physical two-factor or passwordless authentication. It’s virtually unhackable remotely because it requires physical presence to activate. It provides pre-boot authentication by combining BitLocker (Windows) or LUKS (Linux) with pre-boot authentication and require a YubiKey as part of the unlock process.
If you use VeraCrypt, you can set up two-factor decryption using a password plus a YubiKey-stored PGP key or OTP (one-time password). You can also configure your OS to require the YubiKey to log in. Even if someone knows your credentials, they can’t access your machine without the key. Furthermore, suppose your backups are stored in the cloud. In that case, you can secure your Google Drive, Dropbox, iCloud, etc. with a YubiKey as a second factor to prevent unauthorized access—even if your account credentials are compromised.

Regularly Backup Your Data
Another very important aspect of securing your data is ensuring that you regularly backup your files. Backing up your hard disk data ensures that you always have a recoverable version of your files stored in a safe, separate location. The golden rule of backups is often called the 3-2-1 strategy: keep at least three copies of your data, on two different types of media, with one copy stored offsite. This might mean saving files on your main hard disk, backing them up to an external drive, and keeping an encrypted version in a cloud service like Google Drive, Dropbox, or an enterprise-grade storage solution.
Automation is key to ensuring backups happen consistently. Manual backups are easy to forget, but scheduling automated tasks—whether daily, weekly, or in real time—can save you from catastrophe. Most modern backup tools allow you to encrypt your backup sets as well, meaning that even if a cloud provider or physical drive were compromised, your data would remain unreadable without the encryption key.
It’s important to note that the security of your backup is just as crucial as the security of your primary data. If your backup drive is sitting unsecured in a drawer, it can easily be stolen and used to bypass your otherwise airtight digital security. Encrypt your backups, password-protect the storage medium, and keep physical copies in locked environments like safes or secure server rooms. For organizations, implementing versioning—keeping multiple snapshots of data over time—can also help recover from ransomware or data corruption without rolling back to an outdated state.

Secure Erasure and Responsible Drive Disposal
Most people are unaware that deleted data is not entirely lost and it can be easily recovered (where does deleted data go?). When it’s time to retire a hard disk—whether it's due to age, damage, or system upgrades—it's critical to dispose of it in a way that ensures no one can retrieve your data.
Simply deleting files or even formatting the drive doesn’t cut it. These methods only remove references to the data in the file system, but the actual bits remain on the disk until they’re overwritten by new data. That means with basic recovery software, even a novice can retrieve deleted files from a seemingly “clean” drive.
To truly render your data unrecoverable, you need to use secure erasure techniques. Software-based data wiping tools like DBAN (Darik's Boot and Nuke), Blancco, or built-in utilities like diskpart (Windows) and dd (Linux/macOS) can overwrite the entire drive multiple times with random data patterns. This process, known as data sanitization, ensures that even forensic-level tools won’t be able to recover previously stored files.
For organizations dealing with highly sensitive or regulated data—such as health records, financial data, or intellectual property—software-based wiping might not be enough. In such cases, physical destruction is the most foolproof method. This includes shredding the hard drive, drilling holes through the platters, or using industrial-grade degaussers that disrupt the magnetic fields used to store data. While extreme, these methods eliminate any possibility of data retrieval and are often mandated by compliance standards such as HIPAA, GDPR, or ISO 27001.
It’s also important to maintain a proper audit trail during drive disposal, especially in enterprise environments. Documenting when and how drives were wiped or destroyed provides accountability and can protect you from liability in the event of a data breach claim. Certificates of destruction issued by certified IT asset disposal services (ITAD) can also add a layer of legal assurance that the process was handled correctly.
In both personal and professional contexts, failing to erase or destroy retired hard drives properly can lead to data leaks, identity theft, or even corporate espionage. By taking the extra step to securely sanitize or destroy a drive, you close the final door that could otherwise leave your sensitive information exposed.
Conclusion
Protecting your data isn’t complicated—it just takes the right steps and some consistency.
Start with full-disk encryption so your entire drive is unreadable without the right key. Use strong passwords and two-factor authentication to ensure only you can access your system. If you share your device or want extra protection, encrypt sensitive folders separately for added control.
Always set up regular backups—automated if possible—so you don’t lose your files if your drive fails or gets compromised. When it’s time to get rid of a drive, wipe it securely with data-erasure software or physically destroy it. Don’t just delete files and hope for the best.
